2023 Retrospective: Automotive Security
by Alexander Alasjö 2024-05-14
As cars have evolved into sophisticated networks on wheels, they have also become susceptible to cyber threats that can jeopardize passenger safety, data privacy and vehicle functionality. Cyber security is now a cornerstone for safe and reliable vehicle operation, making it clear that security is key to assuring safety.
Security testing of vehicles and vehicle components is a domain where Assured is at the forefront. We have always had automotive security dear to our hearts. Our extensive experience in the automotive cyber security domain is a product of our expertise and our commitment to research in the field of technical cyber security. In the past year, we had the privilege of collaborating with prominent suppliers and OEMs in the automotive industry, dedicating a significant portion of our resources to exploring and fortifying the cyber security of automotive electronics and vehicles.
In this blog post we summarize our experiences and insights from our automotive security engagements in 2023. We will discuss the key challenges we encountered, the trends we observed, and the recommendations we have for the industry. We will also address the regulatory landscape and the implications of cyber security regulations on the automotive industry. This provides a comprehensive overview (from our perspective) of the state of automotive cyber security and hopefully offers valuable insights to anyone interested in automotive security.
This is the third and last blog post in our 2023 retrospective series. In previous posts, we addressed our 2023 retrospectives on IT infrastructure and Active Directory security and Web and Mobile Application Security.
Table of Contents
- Automotive Security Engagements in 2023
- Key Automotive Security Challenges Encountered in 2023
- Automotive Security Trends
- Recommendations for Improving Automotive Security
- Conclusion
Automotive Security Engagements in 2023
At Assured, we engaged heavily in automotive cyber security in 2023. Our team conducted several penetration tests, including both individual components (ECUs) and extensive full-vehicle assessments targeting all cyber security relevant components in various types of vehicles. These vehicles ranged from passenger cars and sports cars to transportation vehicles, each with their own challenges and interesting attack vectors.
Our work in 2023 resulted in the identification and reporting of over 100 vulnerabilities to our clients, a third of which were classified as high or critical risk. These vulnerabilities spanned a wide range of systems, including infotainment units, telematics systems, and other critical components. The findings helped our clients remediate security weaknesses in their vehicle systems, ensuring that they meet regulation requirements for cyber security.
Moreover, our involvement as technical security experts in a type approval audit and witness test was a standout experience. We performed witnessed testing for UNECE R155 test cases, gaining valuable insights into the type approval process and which areas of cyber security are of interest to type approval auditors. This engagement provided us with a deeper understanding of regulatory expectations and industry best practices.
The extensive reports we produced for our clients in the automotive domain, totaling over 250 pages, show both our thoroughness in testing and the extensive issue descriptions and recommendations we provide. These documents are valuable resources for our clients, guiding them in implementing robust cyber security measures and managing risks.
Our experiences during 2023 have expanded our understanding of automotive cyber security and reinforced our commitment to advancing the field. We remain passionate about security research, hosting trainings and performing security assessments/penetration tests to transfer knowledge and improve the security posture of the automotive industry.
Key Automotive Security Challenges Encountered in 2023
Throughout the year we encountered some common issues in automotive security engagements, some of which are familiar from other areas such as application security and network security testing.
Internal networking issues, such as firewall management, access control, and routing, were common. We also observed vulnerabilities in exposed interfaces and services, which could potentially lead to information disclosure and leakage, including internal logs and PII (Personally Identifiable Information).
Debug interfaces were another area of concern. Many systems lacked robust authentication measures, allowing for easy deduction of root passwords and authentication bypass. This exposure could lead to deeper system exploitation but are often hard to exploit in practice due to physical access requirements and other mitigating factors.
The use of weak random number generators or insufficient key material lengths in diagnostic services (Security Access) and wireless key fob rolling codes was also observed. These vulnerabilities could lead to unauthorized access to vehicles and compromise their security. This is quite common for embedded systems where hardware limitations may restrict the use of proper random number generators.
In-car apps on Android Automotive systems, especially from third-party suppliers were found to be built insecurely and not following good security practices. These are interesting attack vectors as they are often connected to the internet and can be exploited remotely. They also infer a privacy risk as they may collect and send sensitive data to third parties.
Internal Networking Issues
Our investigations into internal networking systems of vehicles uncovered several security issues. A wide range of vulnerabilities in this area were observed, from lacking firewall configurations, broken access control, and routing issues to internal network services exposed on external-facing interfaces.
Infotainment and Telematics
The infotainment system is often the most capable unit in the vehicle, having plenty of compute power to simultaneously consume and display information while running third-party and OEM apps for entertainment and connectivity services. This device is often dependent on a telematics gateway, if not built-in, to be able to communicate with the backend via cellular networks. We have seen a common pattern where the infotainment unit is central to the internal networks of the vehicle, often serving as a combined router and firewall/gateway for most Ethernet-based networking. This poses potential risk for several reasons:
- Internal components are denied service if the infotainment unit becomes unresponsive.
- An insecurely configured firewall can lead to compromised sensitive internals.
- Applications and processes with elevated privileges on the infotainment unit may sniff and inject arbitrary data on internal subnets.
- Adjacent devices (including locally attached adversaries) can spoof internal components (IP and MAC addresses) to confuse the router/switch.
Overly Exposed Network Interfaces and Services
A significant type of issue we have found is regarding overly exposed network interfaces and services. Such vulnerabilities could lead to service disruption, manipulation as well as information disclosure or leakage.
For the purpose of entertainment or accessibility, an infotainment unit may offer the passengers various connectivity options, e.g., via Wi-Fi or Bluetooth. Since these connectivity services may in part share the same components as internal network interfaces, confusion can arise and internal services and communication may be exposed, if they are not strictly and properly segmented and access controlled.
For example, Android Auto and Apple CarPlay are popular connectivity services for interaction between smartphones and infotainment units. This interaction opens up new potential attack surface, and is a potential security risk if the Wi-Fi network is not properly segmented from the internal network.
Furthermore, exposed in-car USB ports attached to internal components may allow for arbitrary input devices to be connected, e.g., a keyboard, mouse, or other USB devices. Attaching a USB device could under certain circumstances expose internal services.
Lacking Encryption in Transit
Inspecting traffic within, to and from vehicle components sometimes uncover messages not encrypted in transit, meaning that an observer within the network can see the plain text messages sent. Though most manufacturers employ adequate transport encryption for communication between a vehicle and the backend, we have reported on issues where sensitive information is passed on unencrypted internally, or sometimes logged in plain text.
It should be noted that many (legacy) protocols used in the automotive industry are not designed with security in mind, and may not be easily retrofitted with encryption. This is a challenge for manufacturers who want to modernize their platforms and services, as they need to consider the security implications of using these protocols. That said, some suppliers have taken the initiative to implement secure communication channels, such as TLS, in their products, which is a step in the right direction.
Debug Interfaces
A recurring issue we encountered was in exposed debug interfaces of various automotive systems. A common flaw was the lack of robust authentication mechanisms, which made it possible to obtain credentials or even bypass authentication procedures altogether. This vulnerability is particularly alarming, as it opens up avenues for deeper system exploration and exploitation.
Debug interfaces are often used during development and testing to troubleshoot issues and monitor system performance. However, these interfaces are not always disabled or properly secured before the vehicle is deployed, leaving them vulnerable to unauthorized access.
In some cases, we found that debug interfaces were accessible over standard communication protocols, such as USB or Ethernet, making them easy targets for attackers. This attack vector is often hard to exploit in practice due to physical access requirements and other mitigating factors such as the need for specialized tools, special circumstances or specific knowledge.
Issues with Random Number Generators
In our tests, we observed issues with the use of random numbers in diagnostic services (Security Access seeds) and wireless key fobs. For example, we found instances where the Security Access seeds were insufficiently random or of insufficient lengths, leading to potential unauthorized diagnostic access on certain ECUs. This is a common issue in embedded systems where hardware limitations may restrict the use of proper random number generators, but also an overlooked area where improvements can be made.
Weaknesses in key fob rolling codes were also identified, albeit not easily exploitable. The rolling code is a security feature used in key fobs to prevent replay attacks. However, if the rolling code key generation algorithm is weak or produces predictable results, attackers could potentially gain unauthorized access to the vehicle.
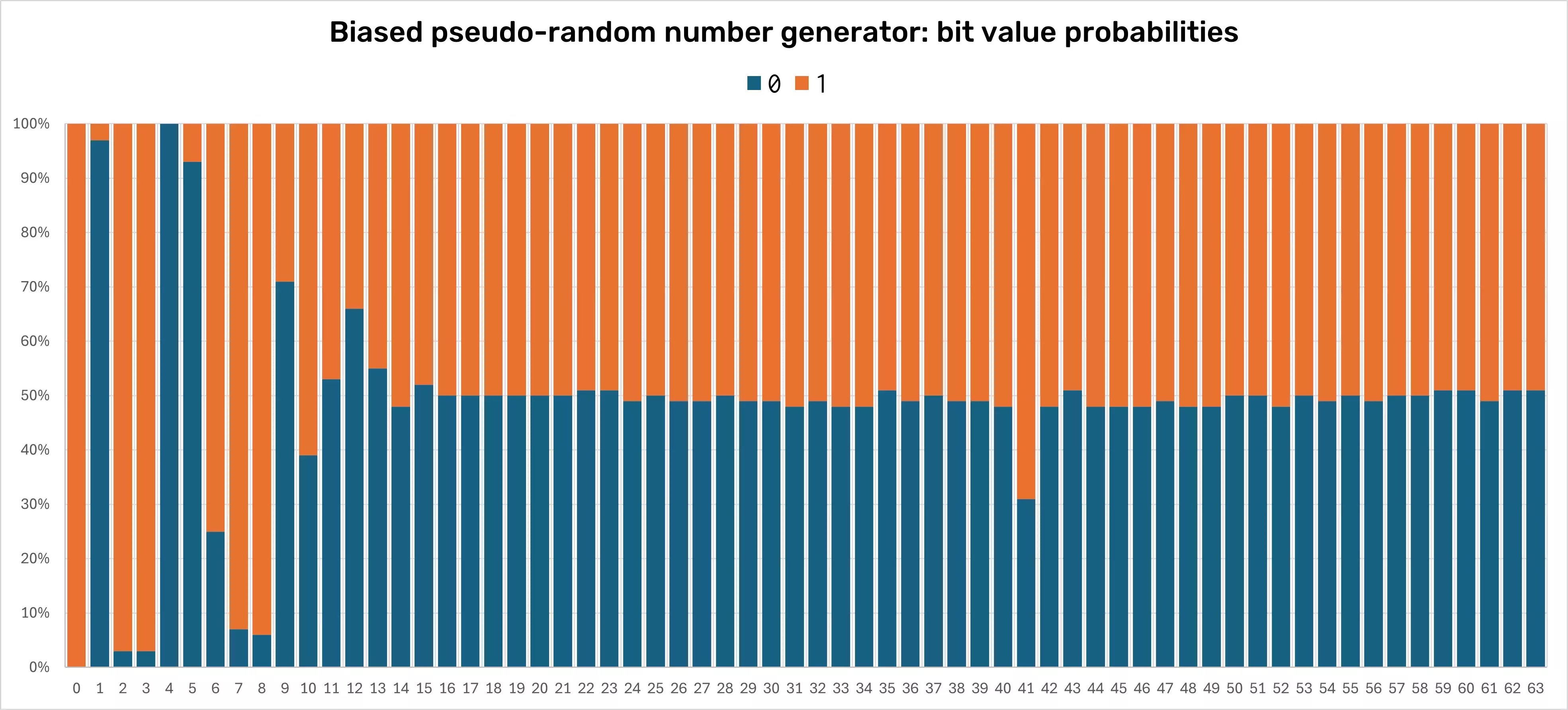
As a telling example, in different engagements we found biased pseudo-random number generators used for the Security Access seeds. The "random" numbers were objectively short, and, after collecting many samples, analysis showed that the effective length was even shorter, as there were evident patterns in the generated numbers. The figure below shows an example diagram of such a biased pseudo-random number generator. Optimally, the probability of a bit value being 1 or 0 should be uniform (near 50 percent) over time. In this example with thousands of samples, some bits are static while some probabilities are skewed quite predictably.
Lacking Hardening on OS level
Another common pattern we found during last year's engagements was related to lacking hardening on the operating system level, where internal networks were not properly segmented, user permissions were not properly restricted, file systems were not encrypted at rest and services were not properly configured.
Capable components with more compute power, such as the infotainment unit, are often running a full-fledged operating system like Linux or Android. We have found these types of systems are often without proper hardening. This may be caused by a lack of awareness of the risks associated with running a general-purpose operating system in a vehicle, or by the complexity of securing such systems. There could also be real-time and safety requirements that make it difficult to implement security measures without affecting performance. Nevertheless, it is interesting to see that some manufacturers are taking steps to secure their systems by implementing secure boot, encrypted file systems and other security measures as a response to regulations and as a proactive security measure.
Automotive Security Trends
It's evident that the landscape of automotive cybersecurity is rapidly evolving. The implementation of new regulations, such as UNECE R155/R156, signify a positive shift towards security awareness in the industry. Automotive manufacturers and suppliers must solve complex challenges to secure their vehicles against an expanding array of cyber threats.
Regulation Impact on the Automotive Industry and Cybersecurity Service Providers
From July 2024, all new vehicles produced must meet cybersecurity requirements to be sold in the EU. The UNECE R155 and R156 regulations set the benchmark for cybersecurity in vehicles, requiring manufacturers to implement robust security measures to protect vehicles against cyber threats. These regulations mandate that manufacturers conduct risk assessments, implement security by design, and establish incident response plans to address cybersecurity incidents. The regulations also require manufacturers to provide software updates to address security vulnerabilities and ensure that vehicles are secure throughout their lifecycle. The implementation of these regulations will help to improve the security of vehicles and protect consumers from cyber threats. Manufacturers must take a proactive approach to cybersecurity to ensure that their vehicles are secure and compliant with the regulations. This includes conducting security assessments, implementing security controls, and monitoring for security incidents.
This sets a high bar for security specialists such as ourselves, as we must ensure that our clients meet these requirements and are prepared for type approval certification. In turn, we need to be well prepared and equipped to conduct comprehensive security assessments, identify vulnerabilities, and provide clear reports aimed both to our clients for remediation and to the type approval auditors for understanding the security posture of the vehicle type.
Recommendations for Improving Automotive Security
Our tests last year identified automotive security challenges in several areas including internal networking issues like firewall management and exposed services leading to potential information leaks, along with vulnerabilities in debug interfaces and weak security in in-car applications, which increased risks of unauthorized access and privacy breaches. Based on these security issues and trends we observed in 2023, here are our recommendations for automotive manufacturers and suppliers to enhance the security of their vehicles. This list is not exhaustive in any way, but rather a starting point for improving the security posture of vehicles:
- Avoid single points of failure in the vehicle's network architecture. Distribute critical functions across multiple components to prevent a single point of failure.
- Disable debug interfaces by default. Ensure that debug interfaces and similar services are disabled by default in production configuration.
- Configure firewalls according to the principle of least privilege. Limit access to internal network services and implement access control lists.
- Configure network services to only listen on intended interfaces/subnets. Ensure that network services are configured to only listen on the intended interfaces and subnets.
- Implement encryption for internal network traffic to protect sensitive information from eavesdropping. Use secure communication protocols, such as TLS, to encrypt internal network traffic.
- Use cryptographically sound, strong random number generators. Implement strong random number generators for cryptographic purposes.
- Harden the operating system of critical components. Implement security measures, such as secure boot, encrypted file systems, and user permissions, to harden the operating system of critical components.
- Conduct security assessments of in-car/third-party applications. Perform security assessments of in-car and third-party apps to identify vulnerabilities and security weaknesses.
Conclusion
Vehicles today are not just modes of transportation but sophisticated networks on wheels, requiring a level of security that matches their complexity. The UNECE R155 and R156 regulations set new benchmarks in the industry, positioning cyber security as a non-negotiable aspect of automotive design and manufacturing. These regulations are not only altering the way vehicles are built but also how they are perceived in terms of safety and reliability.
With our team of seasoned security specialists, Assured is a trusted partner in automotive cyber security. Our experiences have equipped us with a unique perspective on the challenges and opportunities that lie ahead in the automotive security domain. We understand the complexities and nuances of automotive cyber security and are committed to providing our clients with the expertise and solutions necessary to navigate this challenging landscape. Our approach is grounded in deep technical knowledge, a proactive stance on emerging threats, and an understanding of regulatory requirements.
We invite industry executives, manufacturers, and stakeholders to partner with us in driving the future of automotive security. For more information on how Assured can assist your organization in enhancing automotive cyber security, please reach out. Let's collaborate to create a safer, more secure automotive future.
Your Security Assured.